How to troubleshoot Azure Multi-Factor Authentication (MFA)?
Microsoft is spending its efforts largely on applying security measures across their solutions or apps. One of the major security feature is the Multi-Factor Authentication (MFA) in Azure AD that is used to authenticate to certain device, app or service. Once registered for MFA, the user has to put some code sent on his/her mobile phone application called Microsoft Authenticator OR approve/reject the notification received in the same app. This sounds easy but often it ends up in some error while registering user account on MFA. In this blog, i have gathered some most commonly seen MFA errors/issues and their resolutions which might help in fixing it.
Error # 1: You cannot have more than 5 hardware tokens or authenticator apps.
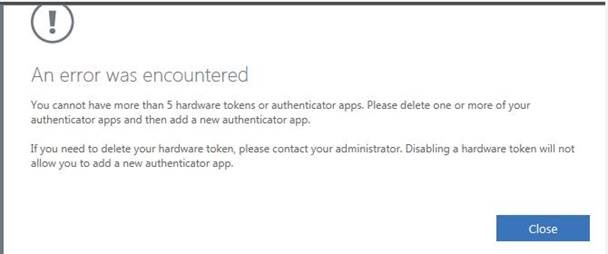
Resolution/Troubleshooting:
As a Helpdesk Admin or System Admin, you first need to check how many devices has been registered on the user’s account. This can be checked from Azure Portal > Azure Active Directory > Search for user > Authentication Methods. If you can get the confirmation from user for any unknown device, you can delete it from here. You can then re-register the user MFA session to get the registration prompt on next sign-in.
Another way to check is to ask user to login from his/her account on https://myaccount.microsoft.com and then go to Security Info. Here, the user can find the devices which is unknown and can be deleted.
Error # 2: Request failed due to exceeding the number of allowed attempts
Resolution/Troubleshooting:
This error usually comes when a user tries multiple times to authenticate but fails. There are certain number of attempts which are allowed and if that exceeds, this error will come up. Most of the time, this error gets fixed by waiting for few hours and trying again after that. Otherwise, System Admins or Helpdesk team can Revoke the MFA sessions from Azure AD portal > Search for user > Authentication Methods.
Error # 3: Unusual MFA registration prompts
Resolution/Troubleshooting:
Your user could end up in a situation where they might be asked for registering MFA methods for themselves even though MFA is disabled (both per-user and CA). This can be really frustrating for System admins to diagnose what exactly is causing MFA to trigger. Here are some troubleshooting steps which might help System Admins or Helpdesk fellows to troubleshoot this issue.
To begin with, do check if Security Defaults is enabled for your Azure AD tenant. If it is enabled, then it will override the CA policy and shall enforce MFA registration to all users. So you should disable it as per your requirements of organization security policies.
If Security Defaults is already disabled, then you need to check if users’ devices have been enabled for MFA registration automatically when joined with Azure AD. You can check this option in Azure AD>Devices>Device Settings. You can disable this option for tenant-wide but you can also do it for specific user by modifying a registry key on that device.
Here is the registry key path: HKLM\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin
Here is the key “BlockAADWorkplaceJoin” whose DWORD value should be 00000001
When that is done, the device needs to be restarted and hopefully it will not be prompted for MFA registration while accessing Microsoft 365 services.


Be First to Comment